Policy overview
A policy is a set of processing rules that are applied to matching traffic. The 5 rule stages are applied to the request in order. Connections to Internet resources are monitored for the duration of the session, and all upstream and downstream traffic is inspected based on your policy rules before being routed back to the appropriate user.
You can define multiple policies to apply different levels of protection and content enforcement to different parts of your organization. Policies consist of five stages: Network, Applications, Web, Threats, and File Filtering.
Figure: Policy overview
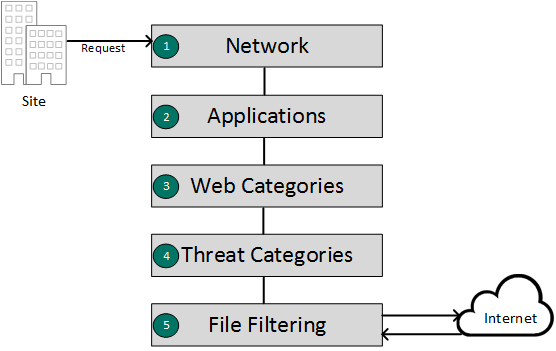
- 1
- Network rules secure traffic at the network level, by applying block, allow, or continue actions for network traffic based on source or destination address, or traffic signatures defined as Services.
- 2
- Application rules provide control over the use of cloud applications by applying block, allow, or continue actions for traffic to and from specified applications. TLS traffic can be decrypted for inspection.
- 3
- Web rules and web exceptions define access rules for web content, applying block, allow, or continue actions for access to websites, based on the category of the site. TLS traffic can be decrypted for inspection. Web exceptions can override the default action for a category for specific client IP addresses and sites.
- 4
- Threat category rules perform deep packet inspection and threat detection to block suspicious traffic. Threat exceptions can override the default category action for specific traffic sources, destinations, services, and threat situations.
- 5
- File filtering and scanning secures file uploads and downloads by performing file reputation analysis, anti-virus scanning, and sandboxing, and applying allow or block actions to specified file types. (Available in a future release.)
Policy rules are processed in sequence they appear above, and the first match found is applied. Policy stages can be configured in any order.
Policy order
Policies are listed in priority order from the top down. When processing traffic, the service checks policies in this order. The first matching policy is used, and no further policies are checked. If more than one policy applies to the same site, the first policy that matches is used.
Use the Drag to move
 handle beside a rule to change its priority in the list.
handle beside a rule to change its priority in the list.
The default policy is the final policy in the list, and always applies to traffic that does not match another policy.