Overview
Dynamic Edge Protection inspects and secures traffic from any connected site or device, using a set of organization-wide policies providing protection against malware, compromises, and inappropriate content.
Figure: Overview of the configuration management and traffic flow for Dynamic Edge Protection
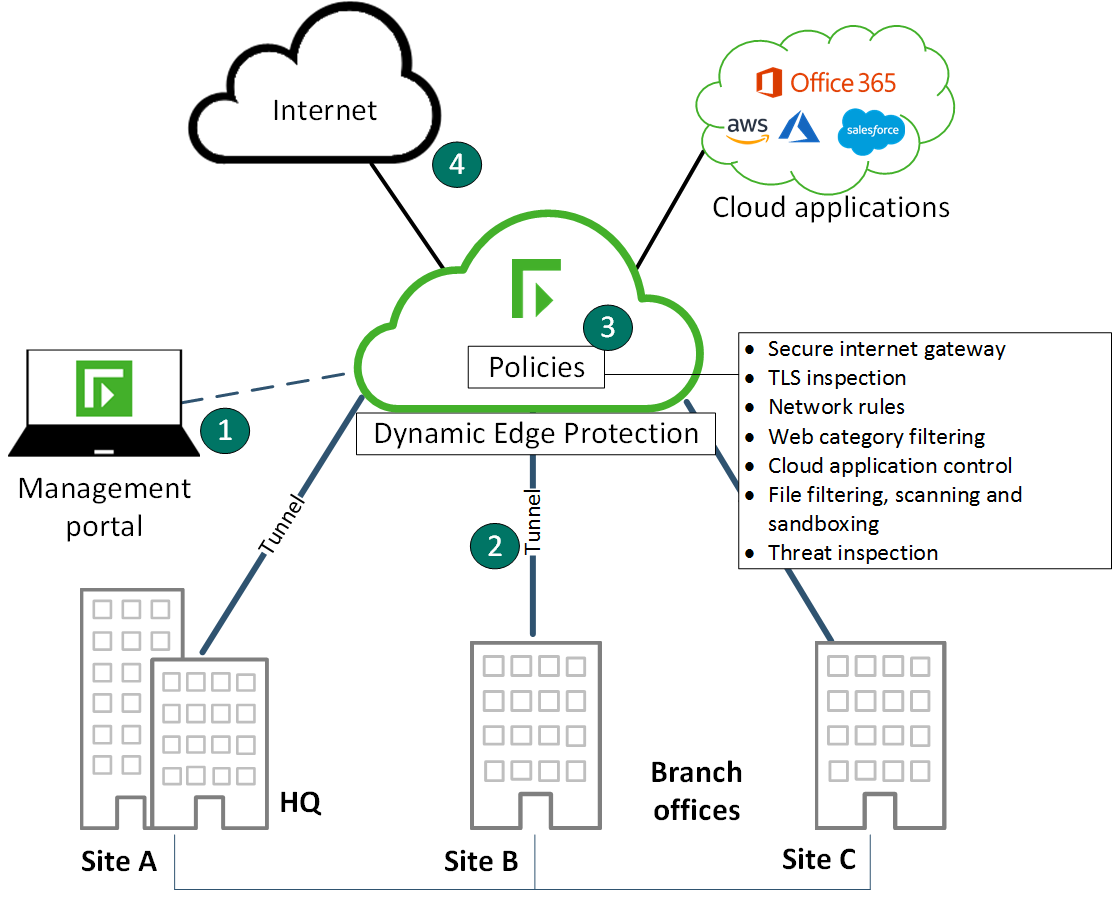
- 1
- The Dynamic Edge Protection management portal is a secure, web-based interface used to configure, maintain, and monitor your Forcepoint product.
- 2
- Protected traffic is directed from your sites to the service via a tunneled connection, or from clients with the Forcepoint Web Security Endpoint installed.
- 3
-
Traffic is processed according to the rules configured in your policies. A policy is a set of rules that inspect traffic. Traffic can be blocked, allowed with threat inspection, or bypassed (allowed with no threat inspection) at each stage of your policy. TLS-encrypted traffic can be decrypted for inspection.
Network address translation (NAT) is performed by Dynamic Edge Protection, and permitted traffic is passed to the requested resource. Decrypted traffic is re-encrypted before being routed to the Internet.
Note: In order for the service to have visibility of end users' IP addresses, tunneled traffic should be directed to the service by your edge device without applying NAT. Visibility of end-user IP addresses is required to apply granular policy rules based on users and groups, and to report on user activity. - 4
- The service is session aware. Connections to Internet resources and cloud applications are monitored for the duration of the session, and all traffic is inspected based on your policy rules before being routed back to the appropriate user.