Data Security is a comprehensive data loss prevention (DLP) system that discovers, monitors, and protects your critical information holdings, whether that data is stored on your servers, currently in use or located in off-network endpoints. Data Security protects against data loss by quickly analyzing data and enforcing customized policies automatically, whether users are on the network or offline. Administrators manage
who can send
what information,
where, and
how. Data Security can also work as a part of Websense TRITON Enterprise to protect the whole of your enterprise.
The Data Security Management Server, which resides on the TRITON management server, is the core of the system, providing complete data loss prevention analysis to the network. In addition, the Data Security Management Server gathers and stores all management statistics. For load balancing purposes, analysis can be shared among a number of Data Security servers. The
protector can provide added blocking capabilities to the loss-prevention system.
The protector works in tandem with the Data Security Management Server. The Data Security Management Server performs discovery (performed by Crawler) and provides advanced analysis capabilities. The protector sits on the network, intercepts and analyzes traffic, and can either monitor or block traffic as needed. The protector supports analysis of SMTP, HTTP, FTP, Generic Text and IM traffic (chat and file transfer). The protector is also an integration point for third-party solutions that support ICAP.
Websense Data Security agents are also an integral part of the system. These agents are installed on the relevant servers (the ISA agent on the Microsoft ISA server, printer agent on the print server, etc.) to enable Data Security to access the data necessary to analyze the traffic from these servers. Agents, such as the Data Endpoint, enable administrators to analyze content within a user's working environment (PC, laptop, etc.) and block or monitor policy breaches.
An example basic deployment has just one management server and one protector. The protector includes several agents, including SMTP, HTTP, FTP, IM, and ICAP. The servers are easily configurable to simply monitor or monitor and protect sensitive data. It is ideal for small to medium businesses with a single Internet egress point. The following illustration is a high-level diagram of a basic deployment of Data Security. Such a deployment is ideal for a smaller- to medium-sized organization with a single Internet egress point. Note that this illustration is intended to show the general distribution of components and does not include network details (such as segmenting, internal firewalls, routing, switching, and so forth).
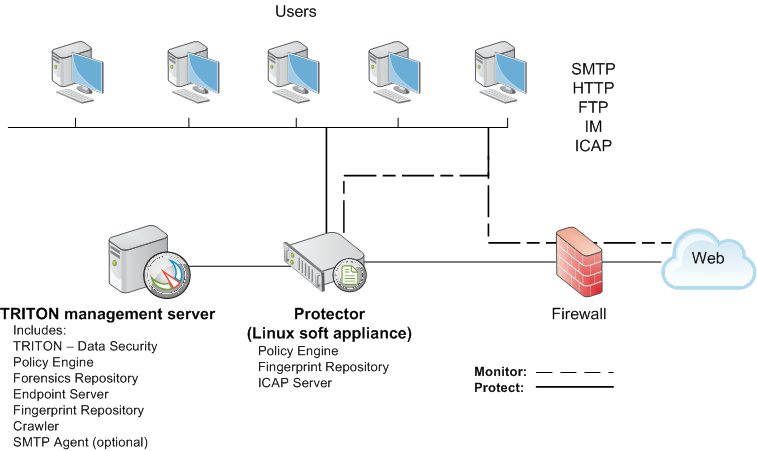
This shows the extended capabilities of Data Security incorporated into a more complex network environment. It shows an extra Data Security server and several additional agents deployed for businesses with larger transaction volumes and numbers of users. Such a deployment is suited for large organizations with multiple Internet egress points distributed over multiple geographical locations. Very large deployments can have multiple Data Security servers and protectors.
 Deployment and Installation Center
Deployment and Installation Center Deployment and Installation Center
Deployment and Installation Center