|

|

|

|

|
|

|
Navigate to the page Settings > Inbound/Outbound > Message Control.
|
|

|
|

|
In the text field Maximum message size, enter a maximum message size in KB, from 1–102400 KB.
|
|

|
Set a maximum message size per connection; mark the check box Limit data size per connection.
|
|

|
In the text field Maximum data size, enter a maximum data size in KB, from 1–204800.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Message Control.
|
|

|
From the section Message Volume Options, mark the check box Limit number of messages per connection.
|
|

|
In the text field Maximum number of messages, enter a maximum number of messages per connection, from 1–65535.
|
|

|
Mark the check box Limit number of recipients per message.
|
|

|
In the text field Maximum number of recipients, enter a maximum number of recipients, from 1–4096.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Message Control.
|
|

|
|

|
In the text field Block message if the percentage of invalid recipients is at least, enter a value for the percentage of invalid recipients that determines if a message is blocked.
|
|

|
Enable the system to send a non-delivery report notification; mark the check box Send non-delivery report (NDR) only if a message is not blocked.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Message Control.
|
|

|
From the section Message Archive Queue, save incoming messages to an archive message queue; mark the check box Enable archive queue storage.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Message Control.
|
|

|
From the section Internal Sender Verification, mark the check box Enable internal sender verification.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Message Control.
|
|

|
From the section Bounce Address Tag Validation, mark the check box Enable Bounce Address Tag Validation.
|
|
?
|
|

|
Click OK.
|
|
?
|
|
?
|
|
?
|
|
?
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
From the section Connection Options, in the text field Simultaneous connections per IP, enter the maximum number of allowed simultaneous connections per IP address, from 1–500.
|
|

|
In the text field Timeout, specify the maximum number of seconds of inactivity allowed before a connection is dropped, from 1–43200.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
From the section Real-time Blacklist Options, mark the check box Perform RBL check.
|
|

|
Save detailed connection information in the appliance mail processing log; mark the check box Save connection details in the mail processing log.
|
|
?
|
|
?
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
From the section Reverse DNS Lookup Options, mark the check box Enable reverse DNS lookup.
|
|

|
|

|
Save detailed connection information in the appliance mail processing log; mark the check box Save connection details in the mail processing log.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
From the section Reputation Service Options, mark the check box Enable Reputation Service.
|
|
?
|
|
?
|
|
?
|
|
?
|
|

|
Save detailed connection information in the appliance mail processing log; mark the check box Save connection details in the mail processing log.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
From the section SMTP Greeting Delay Options, mark the check box Enable SMTP greeting delay.
|
|

|
Save detailed connection information in the appliance mail processing log; mark the check box Save connection details in the mail processing log.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
From the section SMTP VRFY Command Option, mark the check box Enable SMTP VRFY command.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
From the section Email Hybrid Service SMTP Authentication Option, unmark the check box Enable email hybrid service SMTP authentication.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
|

|
Click OK.
|
|
?
|
|
?
|
|
?
|
|
?
|
|

|
Navigate to the page Settings > Inbound/Outbound > Connection Control.
|
|

|
|

|
Click Edit.
|
|

|
In the section IP Address Group, add a predefined IP address group; from the field IP address file, click Browse and navigate to the desired text file.
|
|

|
Manually add IP address entries; in the field IP address, enter an individual IP address and click >.
|
|
Any changes made here to an IP address group are reflected on the page Settings > Inbound/Outbound > IP Groups.
|
|

|
|

|
|

|
Click OK.
|
|

|
Click OK.
|
|
?
|
|
?
|
|
?
|
From the pull-down menu Per page, select the number of signing key entries per page, between 25 and 100.
|
|

|
Click Search.
|
|

|
Clear search results; click Show all keys.
|
|

|
|

|
In the text field Key name, enter a name for your key.
|
|

|
Click OK.
|
|

|
Generate a new key; click the button Generate Key.
|
|

|
Click OK.
|
|

|
|

|
Click Browse and navigate to the desired key file.
|
|

|
Click Open.
|
|

|
|

|
|
Link that opens a Generate DNS Text Record dialog box. See Generating a DNS text record (public key).
|
|
|
?
|
From the pull-down menu Per page, select the number of signing rule entries per page, between 25 and 100.
|
|

|
Click Search.
|
|

|
Clear search results; click Show all rules.
|
|

|
|

|
In the text field Rule name, enter a name for your rule.
|
|

|
(Optional) Include the identity of the user or agent for whom the message is signed; mark the check box Include user identifier.
|
|

|
|

|
In the text field Selector, enter the domain name selector.
|
|

|
From the pull-down menu Signing key, select the signing key to associate with this rule from the list of existing keys.
|
|

|
Click Advanced Options.
|
|
?
|
From the pull-down menu Algorithm, select an encryption algorithm.
|
|
?
|
|
?
|
In the field Additional headers, include other headers as a comma-separated list.
|
|
?
|
t lets you add a signature creation timestamp.
|
|
?
|
x lets you specify a signature expiration time in seconds.
|
|
?
|
z adds the list of signed header fields to the signature.
|
|

|
From the pull-down menu Signing rule options, select either Sign email messages or Do not sign email messages.
|
|
?
|
For example, if you select Sign email messages, then email from the addresses in the list is signed. Email from other addresses is not signed.
|
|
?
|
If you select Do not sign email messages, then email from the addresses in the list is not signed, and email from all other users is signed.
|
|

|
Click OK.
|
|

|
|

|
Click Browse and navigate to the desired key rule file.
|
|

|
Click Open.
|
|

|
|

|
|

|
|

|
|

|
Click Add.
|
|
The IP address or group that you enter here must not already be defined in the Trusted IP Addresses group (Settings > Inbound/Outbound > IP Groups) or appear in the connection control Allow Access List (Settings > Inbound/Outbound > Connection Control).
|
|

|
In the field Check for header, enter header text to match for true source IP detection.
|
|

|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Enforced TLS Connections.
|
|

|
Click Add.
|
|

|
In the text field Name, enter a name for your enforced TLS connection.
|
|

|
From the pull-down menu Priority order, select a priority order for the connection.
|
|
?
|
Encrypt, the minimum enforcement level, used in all security levels
|
|
?
|
Encrypt and check CN, validation of a certificate's common name
|
|
?
|
Verify, validation that the certificate is from a trusted CA
|
|
?
|
Verify and check CN, validation of the certificate's common name and that the certificate is from a trusted CA
|
|
To use the two "verify" options, you must have imported a trusted CA certificate. See Managing Transport Layer Security (TLS) certificates.
|
|
?
|
|
?
|
|

|
Click OK.
|
|

|
|

|
Enable the directory harvest attack prevention function; mark the check box Limit the number of messages/connections per IP every.
|
|

|
If you have enabled the directory attack prevention option, you can also enable settings to block an IP address when a specific set of recipient conditions occurs; mark the check box Block the IP address for and enter the time interval during which to block an IP address.
|
|

|
Click OK.
|
|

|
|
?
|
Fail. The domain owner's SPF record does not authorize the sender host machine to send email for the domain.
|
|
?
|
SoftFail. The domain owner's SPF record allows the sender host machine to send email for this domain, even though the host is not explicitly authorized to do so.
|
|
?
|
Neutral. The domain owner's SPF record makes no statement as to whether the sender host machine is authorized to send email for the domain.
|
|
?
|
None. The lack of definitive SPF information prevents an SPF check (e.g., an SPF record does not exist).
|
|
?
|
PermError. A permanent error occurs (e.g., the SPF record has an invalid format).
|
|
?
|
TempError. A transient error occurs (e.g., a DNS timeout).
|
|

|
|
ï¡ï€®ï€ˆ
|
Mark the check box Bypass SPF validation for senders in the following domain group
|
|
ï¢ï€®ï€ˆ
|
Select a sender domain from the pull-down menu Domain group
|
|

|
In the section Outbound Relay Options, select the relay setting for senders in protected domains when SMTP authentication is not required; Allow relays only for senders from trusted IP addresses or Allow all outbound relays.
|
|

|
In the section Internal Relay Options, select the relay setting for mail between protected domains when SMTP authentication is not required; Allow relays only for senders from trusted IP addresses or Allow all internal relays.
|
|

|
Click OK.
|
|
?
|
|

|
Click Copy.
|
|

|
Click Add.
|
|

|
In the field Name, enter a name for your new route.
|
|

|
From the pull-down menu Route order, select an order number to determine the scanning order of the route.
|
|

|
From the pre-defined domains in the pull-down menu Domain group, select a destination domain.
|
|
?
|
To add a new user directory, click Add user directory.
|
|
ï¡ï€®ï€ˆ
|
Click Add to open the Add SMTP Server dialog box
|
|
ï£ï€®ï€ˆ
|
Mark the check box Enable MX lookup to enable the MX lookup function
|
|
|
ï¡ï€®ï€ˆ
|
Ensure email traffic uses opportunistic TLS protocols; mark the check box Use opportunistic Transport Layer Security (TLS)
|
|
ï¢ï€®ï€ˆ
|
Ensure that users supply credentials; mark the check box Require authentication
|
|

|
Click OK.
|
|
The Protected Domain group defined on the page Settings > Users > Domain Groups should not be used to configure delivery routes if you need to define domain-based delivery routes via multiple SMTP servers.
|
|

|
Click Add.
|
|

|
In the field Name, enter a name for your new route.
|
|

|
From the pull-down menu Route order, select an order number to determine the route's scanning order.
|
|

|
From the pre-defined domains in the pull-down menu Domain group, select a destination domain.
|
|

|
|
ï¡ï€®ï€ˆ
|
Click Add.
|
|
ï£ï€®ï€ˆ
|
Mark the check box Enable MX lookup to enable the MX lookup function.
|
|
|
ï¡ï€®ï€ˆ
|
Enable email traffic to use opportunistic TLS protocol; select Use opportunistic Transport Layer Security (TLS).
|
|
ï¢ï€®ï€ˆ
|
Ensure that users supply credentials; select Require authentication.
|
|

|
On the page Settings > Inbound/Outbound > Address Rewriting, click the Inbound Messages tab or the Outbound and Internal Messages tab to display the settings.
|
|

|
|

|
|
?
|
Mark the check box Individual email address or domain rewrite entry and enter the original recipient address and the rewrite address in the appropriate entry fields.
|
|
?
|
If you have an existing email or domain address rewrite entry file, mark the check box Email address or domain rewrite entry file and browse to the file File size may not exceed 10 MB.
|
|

|
Click OK.
|
|

|
On the page Settings > Inbound/Outbound > Address Rewriting, click the Inbound Messages tab or the Outbound and Internal Messages tab to display the settings.
|
|

|
|
?
|
Mark the check box Individual email address or domain rewrite entry and enter the original sender address and the rewrite address in the appropriate entry fields.
|
|

|
Click OK.
|
|

|
On the page Settings > Inbound/Outbound > Address Rewriting, click the Inbound Messages tab or the Outbound and Internal Messages tab to display the settings.
|
|

|
|

|
|

|
On the page Settings > Inbound/Outbound > Address Rewriting, click the Inbound Messages tab or the Outbound and Internal Messages tab to display the settings.
|
|

|
|
?
|
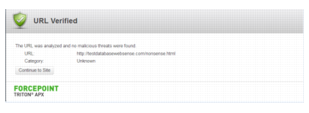
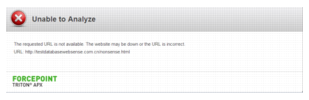
If the protocol is not supported. Supported protocols are HTTP, HTTPS, and FTP. If you have selected the option Allow the recipient to follow links with an unsupported protocol, the user can proceed to view the page if desired; otherwise, the user cannot access the page.
 |
|
ï¡ï€®ï€ˆ
|
Activate the URL sandbox function; mark the check box Analyze suspicious URLs.
|
|
ï¢ï€®ï€ˆ
|
If the URL sandbox is enabled, allow users to click unclassified URL links; mark the check box Allow the recipient to follow links to unclassified URLs.
|
|
ï£ï€®ï€ˆ
|
Allow users to click a link that may redirect to a site with an unsupported protocol; mark the check box Allow the recipient to follow links with an unsupported protocol.
|
|
ï¤ï€®ï€ˆ
|
|
ï£ï€®ï€ˆ
|
Activate the URL sandbox function for these addresses; mark the check box Analyze suspicious URLs.
|
|
ï¤ï€®ï€ˆ
|
If the URL sandbox is enabled, allow the specified users to click unclassified URL links; mark the check box Allow the recipient to follow links to unclassified URLs.
|
|
ï¥ï€®ï€ˆ
|
Allow users to click a link that may redirect to a site with an unsupported protocol; mark the check box Allow the recipient to follow links with an unsupported protocol.
|
|
ï¦ï€®ï€ˆ
|
|

|
Enable the sandbox to examine URLs even if they appear in a message that contains the digital signature of a trusted sender; at the bottom of the section URL Sandbox, mark the check box Analyze suspicious URLs that appear in digitally signed email.
|
|

|
|

|
Click OK.
|
|
?
|
Phishing Rules, which contains a list of all your phishing rules. A default rule applies to domains that are not included in any other defined rule. See Adding a phishing detection rule.
|
|
?
|
Phishing Education Pages, which contains a list of all the education pages you have defined. A default page applies when a custom page is not specified for a phishing rule. See Creating a phishing education page.
|
|

|
On the Phishing Rules tab, click Add Rule.
|
|

|
In the field Phishing rule name, enter a name for the rule.
|
|

|
In the field Domain names, specify the domains to which this rule applies.
|
|
?
|
|
?
|
|
ï¡ï€®ï€ˆ
|
Click Add User Exception.
|
|
ï¢ï€®ï€ˆ
|
In the text field Description, enter a brief description of this exception.
|
|
ï£ï€®ï€ˆ
|
In the text field Email addresses, specify the email addresses for the users or groups to whom this exception applies.
|
|
?
|
|
?
|
|
ï¥ï€®ï€ˆ
|
Click Add.
|
|

|
Click OK.
|
|

|
On the Phishing Rules tab, click Save to Cloud Service.
|
|

|
On the Phishing Education Pages tab, click Copy Page.
|
|

|
Click OK.
|
|

|
|

|
In the text field Page title, specify a title for the page.
|
|

|
Click OK.
|
|
If you receive an error message regarding a synchronization problem with the cloud service, click Save to Cloud Service on the tab Phishing Education Pages to send your phishing education page settings to the email hybrid service.
|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|
Click a queue name in the Queue List to view and manage the messages in the queue. See Viewing a message queue.
|
|
|
From the Status column, click Referenced to display a list of the email functions that use the queue. During a queue move operation, an icon in this column indicates whether the move is in progress or has failed.
|
|
|
Indicates the total number of messages in the queue. The number of messages a delegated administrator sees may be less than the total displayed in this column, depending on the permissions granted to that administrator.
|
|
|
Displays the location of queue storage (Local, via Network File System [NFS], or via Samba).
|
|
|
Contains a link to a page displaying the queue's current settings. Click this Edit link to change any queue settings.
|
|

|
|

|
In the text field Queue name, enter a name for the new queue.
|
|
?
|
|
?
|
Use the NFS protocol for file storage; click Via Network File System (NFS). Enter the IP address or hostname of the storage location, along with its shared path.
|
|
?
|
Use Samba to facilitate file storage; click Via Samba.
|
|
?
|
|
?
|
|
?
|
|

|
Click OK.
|
|

|
|

|
|
?
|
|
?
|
Click Clean to clear the current date/time calendar selection.
|
|
?
|
Click Today to set the calendar date to today's date.
|
|
?
|
Click the arrow to the right of the View date/time range to display the desired queue items.
|
|

|
|

|
From the pull-down menu, click a category on which to search; ID, Subject, Sender, Recipient, Policy/Rule, Processed By, or All.
|
|

|
Click Search.
|
|
?
|
From the pull-down menu per page, select the number of messages to display on each page; 25, 50, or 100.
|
|
Click the link to display the View Message page for viewing message information and contents. See Viewing a message in a queue.
|
|||||||||||||
|
Click View Incident to open the DLP incident information in the Data module, where the message was processed.
|
|||||||||||||
|
Type of message (for example, spam, virus, exception, commercial bulk, advanced malware detection - cloud, advanced malware detection - on-premises, spoofed email, URL analysis, encryption error, or decryption error).
|
|||||||||||||
|
|
?
|
|
?
|
Click Clean to clear the current date/time calendar selection.
|
|
?
|
Click Today to set the calendar date to today's date.
|
|
?
|
Click the arrow to the right of the View date/time range to display the desired queue items.
|
|

|
|

|
From the pull-down menu, click a category on which to search; ID, Subject, Sender, Recipient, Policy/Rule, Processed By, or All.
|
|

|
Click Search.
|
|
?
|
From the pull-down menu per page, select the number of messages to display on each page; 25, 50, or 100.
|
|
Click the link to display the View Message page for viewing message information and contents. See Viewing a message in a queue.
|
|||||||||||||
|
Click View Incident to open the DLP incident information in the Data module, where the message was processed.
|
|||||||||||||
|
Queue in which the message is stored (for example, spam, virus, exception, encryption-fail, or decryption-fail).
|
|||||||||||||
|
Type of message (for example, spam, virus, exception, commercial bulk, advanced malware detection - cloud, advanced malware detection - on-premises, spoofed email, URL analysis, encryption error, or decryption error).
|
|||||||||||||
|
|
?
|
|
?
|
Click Clean to clear the current date/time calendar selection.
|
|
?
|
Click Today to set the calendar date to today's date.
|
|
?
|
Click the arrow to the right of the View date/time range to display the desired queue items.
|
|

|
|

|
From the pull-down menu, click a category on which to search; ID, Subject, Sender, Recipient, Processed By, Reason for Delay, or All.
|
|

|
Click Search.
|
|
?
|
From the pull-down menu per page, select the number of messages to display on each page; 25, 50, or 100.
|
|
Click the link to display the View Message page for viewing message information and contents. See Viewing a message in a queue.
|
|||
|
Click View Incident to open the DLP incident information in the Data module, where the message was processed.
|
|||
|
|||
|
?
|
|

|
Send a notification regarding the unprocessed message; mark the check box Send notification to enable the Notification Properties section.
|
|
?
|
|
?
|
|
?
|
|

|
In the text field Subject, specify the subject line of your notification message.
|
|

|
In the text field Content, enter the body of your notification message.
|
|

|
Attach the original message to the notification message; mark the check box Attach original message.
|
|

|
Click OK.
|
|

|
In the field Retry interval, enter the time for the message retry interval, in minutes.
|
|

|
In the field Maximum retry period, enter the time for the maximum period for retrying message delivery, in minutes.
|
|

|
In the field Notification email address, enter an email address to which to send notifications that a non-delivery report (NDR) cannot be delivered to the original sender at the end of the retry period.
|
|

|
Click OK.
|
|

|
|

|
In the text field Traffic shaping group name, enter a name.
|
|

|
From the pull-down menu Order, specify the location in which this group should appear in the traffic shaping group list.
|
|

|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|
?
|
|

|
In the field Maximum number of concurrent connections, enter the maximum number of simultaneous message deliveries to an individual routing address.
|
|

|
In the field Maximum number of messages per connection, enter the maximum number of messages per connection within a defined time period.
|
|

|
In the field Maximum number of recipients, enter the maximum number of message recipients per message delivery.
|
|

|
Use an SMTP session cache; mark the check box Enable SMTP session cache.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Encryption.
|
|

|
|

|
Use only TLS for message encryption; from TLS Encryption Backup Options, select Use TLS only (no backup encryption method; message is queued for later delivery attempt).
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Encryption.
|
|

|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Encryption.
|
|

|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Encryption.
|
|

|
|
ï¢ï€®ï€ˆ
|
Use the MX lookup feature; mark the check box Enable MX lookup.
|
|
ï£ï€®ï€ˆ
|
Click the arrow to the right of the Add Encryption Server box to add the server to the Encryption Server List.
|
|

|
In the pull-down menu Encrypted IP address group, specify an IP address group if decryption is enabled or if encrypted email is configured to route back to the email software.
|
|

|
Configure users to present credentials to view encrypted mail; mark the check box Require authentication and supply the desired user name and password in the appropriate fields.
|
|

|
In the field Encryption X-Header, specify an x-header to be added to a message that should be encrypted.
|
|

|
In the field Encryption Success X-Header, specify an x-header to be added to a message that has been successfully encrypted.
|
|

|
In the field Encryption Failure X-Header, specify an x-header to be added to a message for which encryption has failed.
|
|
?
|
Mark the check box Send messages to queue.
|
|
?
|
Mark the check box Send notification to original sender.
|
|
?
|
Include the original message as an attachment to the notification message; mark the check box Attach original message.
|
|
?
|
Deliver the message that failed the encryption operation; select Deliver message.
|
|
?
|
|

|
Decrypt encrypted messages; mark the check box Enable decryption
|
|

|
|
?
|
In the field Content type, enter the message content types to decrypt, separated by semicolons.
|
|
?
|
In the field X-Header, specify a message x-header that identifies a message to decrypt.
|
|
?
|
In the field Decryption X-Header, specify an x-header to be added to a message that should be decrypted.
|
|
?
|
In the field Decryption Success X-Header, specify an x-header to be added to a message that has been successfully decrypted.
|
|
?
|
In the field Decryption Failure X-Header, specify an x-header to be added to a message for which decryption has failed.
|
|
?
|
Forward a message that has failed decryption to a specific queue; mark the check box On decryption failure and select a queue for these messages from the pull-down menu.
|
|

|
Click OK.
|
|

|
Navigate to the page Settings > Inbound/Outbound > Encryption.
|
|

|
|

|
|
Secure messaging uses the same port configured for the Personal Email Manager portal (Settings > Personal Email > Notification Message).
|
|
?
|
|
?
|
|
?
|
Internal domain email addresses only. Only email addresses within your organization's protected domains may be specified as recipients.
|
|
?
|
Internal and external domain email addresses (at least one internal email address required). Email addresses outside your organization's protected domains may be specified as recipients, but at least one address within your domains must be entered (default selection).
|
|
?
|
In the field Sender, enter one sender address for the notification.
|
|
?
|
In the field Subject, enter an email subject.
|
|

|
After you have configured your notification message, click Preview Message to view it.
|
|

|
Click OK.
|