|

|

|

|
v8.3 Release Notes for On-Premises TRITON AP-EMAIL : New in version 8.3
|


|

|

|

|
v8.3 Release Notes for On-Premises TRITON AP-EMAIL : New in version 8.3
|
|
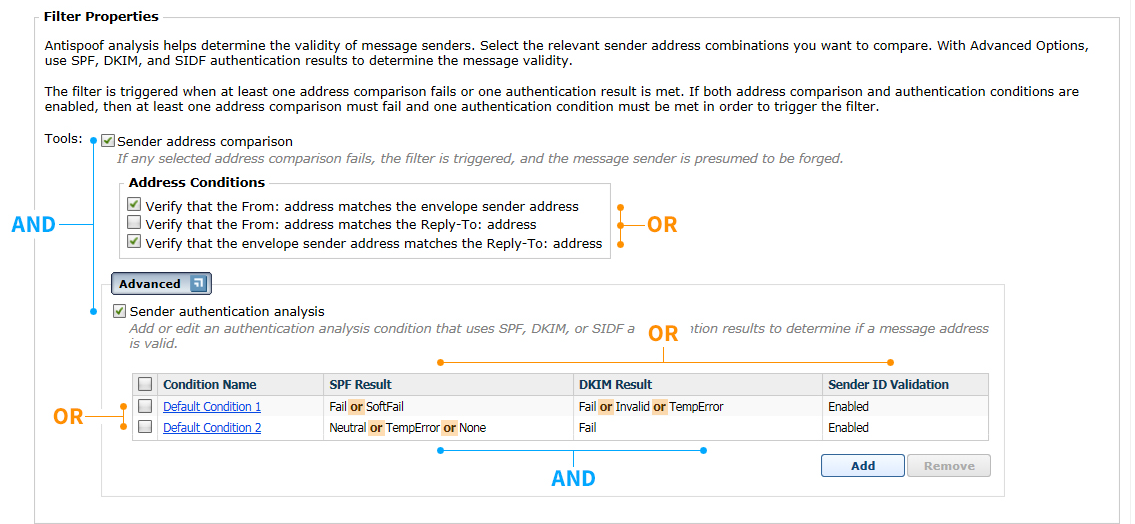
1.
|
Creating a new URL analysis filter in the Main > Policy Management > Filters page (URL analysis in TRITON AP-EMAIL Administrator Help)
|
|
2.
|
Creating a URL analysis filter action in the Main > Policy Management > Actions page (Managing filter actions in TRITON AP-EMAIL Administrator Help)
|
|
3.
|
Adding a new rule on the Main > Policy Management > Policies > Add (or Edit) Policy page using your new URL analysis filter and filter action (Adding a rule in TRITON AP-EMAIL Administrator Help).
|

|

|

|

|
v8.3 Release Notes for On-Premises TRITON AP-EMAIL : New in version 8.3
|